OT Hunt: clearSCADA

Welcome to the 18th installment of “OT Hunt” where we delve into the world of ICS/OT devices connected to the internet. The primary aim of this series is to raise awareness within the ICS community and serve as a wake-up call for both asset owners and ICS/OT vendors to fortify their assets against potential cyber threats.
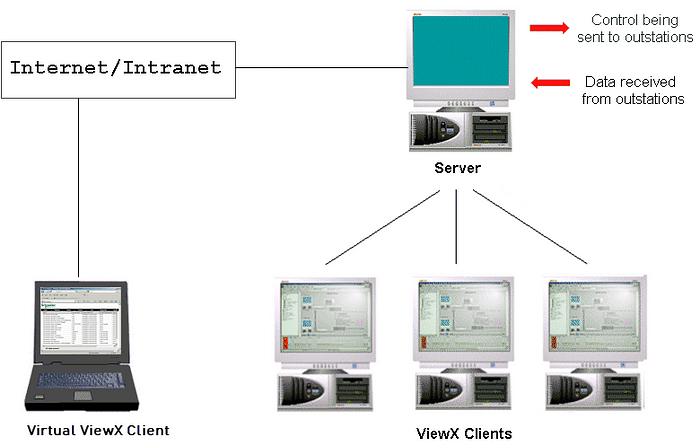
In this installment, we focus on Geo SCADA Expert, formerly known as ClearSCADA — a product by Schneider Electric. Geo SCADA Expert is a Supervisory Control and Data Acquisition (SCADA) system, typically accessed by a client called ViewX. However, it can also be accessed by OPC clients, Citrix, and many other third-party clients.
Using the dork clearscada in Shodan yielded 4 results. However, the advantage of a favicon search over keyword searches, in my opinion, is that it yields more web interfaces on port 80. The hash for this favicon is fixed for a given product—in our case, ClearSCADA! This search by favicon yielded an astounding 2,741 results. The dork used was:
http.favicon.hash:487597720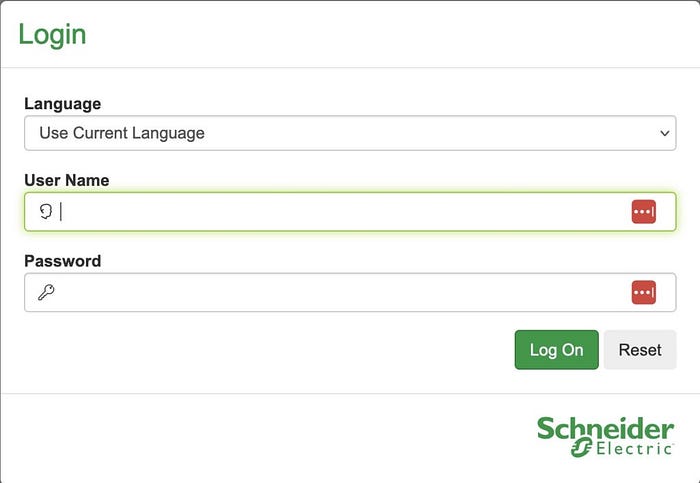
These web interfaces, unfortunately, have varied security postures. Some lack proper access control mechanisms, allowing anyone to view monitoring and diagnostic information without restriction. Additionally, some of these machines have Remote Desktop Protocol (RDP) open, potentially enabling adversaries to exploit this service to gain network access. For more on this, check out MITRE Technique Remote Services T0886. It’s alarming that we don’t fully know what’s running behind this SCADA.
Further digging through other search engines revealed additional ClearSCADA machines with SSH, VNC, SNMP, and FTP services open. I haven’t checked whether these services are accessible without credentials or if they use default passwords. I will leave this task to my tool, ICSRank, which is set to be released this year. Be sure to visit ICSRank.com often to check for updates. It’s designed to discover any attack surface for OT devices and map the found issues to the MITRE matrix.

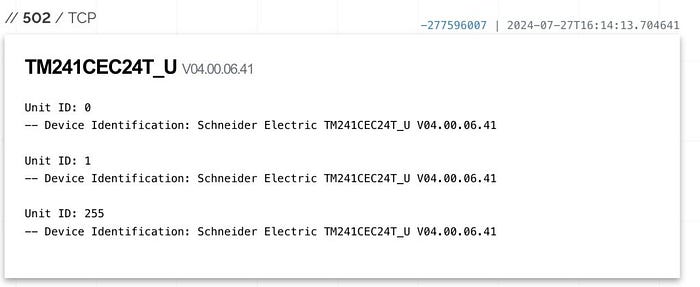
Some ClearSCADA hosts also have Modbus port 502 open. The valuable thing about Modbus protocol information is that it reveals the PLC name — such as the TM241CEC24T Logic Controller from Modicon — which adds an extra layer of intelligence to our OSINT.
It’s important to note that there has been a precedent where attackers utilized RDP connections to hack an OT network. This happened in the Triton attack, which you can read more about here.
I’m going to stop now — this is enough OSINT digging for one session. Remember, there are 2,000 ClearSCADA hosts on the internet. I urge asset owners to watch out and ensure their OT assets are securely configured. While it’s challenging to identify the asset owner using Shodan data alone, I’m committed to finding a solution.
In closing, I invite you to explore our project, ICSRank — a unique tool tailored for the ICS/OT domain, exemplifying our commitment to enhancing ICS/OT cybersecurity. With its capabilities to Discover, Assess, and Secure, ICSRank stands as a vital resource in fortifying ICS/OT environments against cyber threats.
